Which Certificate is my Domain Controller using for LDAPS?
I encountered a Computer Certificate on a Domain Controller which was about to expire soon, and needed to replace it.
After some searching I found two options:
- Add a new Certificate in the Computer store and restart the Domain Controller
- Add a new Certificate in the ADDS Service specific store, and don’t restart the Domain Controller (ADDS should detect new Certificate in service store, and automatically pick up this after some time).
The Certificate wasn’t expiring immediately, so I opted for the first option: add a Certificate in the Computer store and wait for restart during maintenance hours.
After I had added the Certificate, I was curious as to which Certificate would be used by ADDS (there were now two certs in the store, one expiring soon and one expiring later). Started searching for a description of this process, and found it on a microsoft support KB: KB321051
Excerpt:
- AD DS preferentially looks for certificates in [the ADDS/NTDS Service store] over the Local Machine’s store.
- AD DS detects when a new certificate is dropped into its certificate store and then triggers an SSL certificate update without having to restart AD DS or restart the domain controller.
- A new rootDse operation that is named renewServerCertificate can be used to manually trigger AD DS to update its SSL certificates without having to restart AD DS or restart the domain controller.
- Finally, if a Windows Server 2008 or a later version domain controller finds multiple certificates in its store, it automatically selects the certificate whose expiration date is furthest in the future. Then, if your current certificate is approaching its expiration date, you can drop the replacement certificate in the store, and AD DS automatically switches to use it.
I wanted to confirm usage of the Certificate whose expiration date is furthest in the future, but couldn’t find an easy way of achieving this.
Ended up using this method:
- Signed in to an administrative server (with port TCP636 open to the Domain Controller).
- Activated CAPI2-logging.
- Started ldp.exe from command line.
- Connected ldp to the Domain Controller with FQDN:
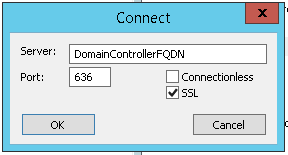 6. Checked the CAPI2-log for an Event with Event ID: 11 and Task Category: Build Chain (under Details -> UserData -> CertGetCertificateChain -> Certificate -> [fileRef] there will be a reference to a .cer file with the Certificate thumbprint as file name).
6. Checked the CAPI2-log for an Event with Event ID: 11 and Task Category: Build Chain (under Details -> UserData -> CertGetCertificateChain -> Certificate -> [fileRef] there will be a reference to a .cer file with the Certificate thumbprint as file name). - Confirmed that the thumbprint of my new Certificate matched the detected thumbprint.
Conclusion: My Windows Server 2012 R2 Domain Controller selected the correct Certificate for LDAPS connections.