Scan Terraform or Bicep in your code editor

TL;DR
Install and enable addons to VSCode for increasing your security posture already before any code is committed to any repository. Checkov and TFSec are two simple and free options you can use.
Background
When writing infrastructure as code there are many pitfalls and security misconfigurations you can make. It it easy to accidentally omit a PaaS firewall config, or neglect to enable encryption. This can be fixed in a later step, like a workflow or pipeline, or it might never be fixed. Maybe you have guardrails where you work that prevent you from such misconfigurations, or you might even be omitting these on purpose. In the end, though, these misconfigurations should probably not end up in your production infrastructure.
These basic misconfigurations add up, and reduces your Cloud Security Posture, increasing your chance of breach or data loss. You can take small steps to alleviate this, and it starts in your IDE!
Part of the solution
As a start, you can install and enable addons in Visual Studio Code. Several Static Application Security Testing (SAST) tools are available in this IDE, and some of them are free.
Part of a good DevSecOps methodology includes scanning your code early. This increases the likelyhood of fixing vulnerabilities or misconfigurations at an earlier stage in your process. There are many benefits of adopting these tools and processes.
- Shift security left
- Avoid costly security reconfigurations after deployment
- A more holistic approach to infrastructure security
- Heightened security awareness
- The total sum of security focus in you chain is increased
- Security misconfigurations might be avoided even before getting pushed to git
I might write a more in-depth post on DevSecOps benefits later, but for now these benefits will do as a motivating factor for adopting part of the process.
The tools
Because they are free, and can do some good scans of your iac code, I have chosen TFSec and Checkov to do my testing. These tools have distinct security policies, and will most likely expose different vulnerabilities. This is good, and leads to a more complete picture than if we used only one of them by themselves.
They can slow down your IDE, though, so be aware of the implications when enabling them. The security benefit outweighs the slowness drawback, so I am using several at the moment.
Checkov
Checkov scans cloud infrastructure configurations to find misconfigurations before they’re deployed. This includes Terraform, Bicep, Kubernetes manifests, and several other areas.
Checkov uses a common command line interface to manage and analyze infrastructure as code (IaC) scan results across platforms such as Terraform, CloudFormation, Kubernetes, Helm, ARM Templates and Serverless framework.
You can use Checkov in many of your DevOps process steps, and it will improve your security awareness. It might also improve your cloud security posture if you choose to implement its recommendations.
Before installing the extension, you need to have Python 3.7 available. I assume it also supports newer versions, but haven’t confirmed this. Python is easily installed with Chocolatey, as I have adopted for some of my software needs. Chocolatey will also enable you to update your software more often, as it streamlines the process more like the package manager apt/apt-get does for Ubuntu.
Run choco install python to install the latest version with Chocolatey.
To use Checkov in VSCode you must first create a user at Bridgecrew, and generate an API token for inputting in your VSCode configuration.
After you have you API token available, you can download and install the extension directly from VSCode marketplace.

Navigate to the Checkov extension settings, and input your API token there.

After this has been done, you can start using Checkov in your daily IaC practices. It will automatically start with each file you write, and will scan on open or whenever you save the current file.
I found that there are some annoying popups whenever Checkov does not support the current file, but this can easily be disabled from the extension settings.
I also use the latest version of Checkov, but you might consider using a pinned version if you have some form of Checkov later in the process. This might also save some time in updating all the time, which it does. There is often a new version that needs to be installed, but the process is quick.
Exclusions
You can skip checks by adding an inline comment like so (storage account ficticious example):
resource "azurerm_storage_account" "sa" {
default_action = "Allow" #checkov:skip=<check_id>:<suppression_comment>
}
TFSec
TFSec is a somewhat simpler tool than Checkov, as it is only a local scan. There is no API, and no user account necessary. You still need to install TFSec, though, and we will get to that shortly.
TFSec uses static analysis of your terraform code to spot potential misconfigurations. This is specific to Terraform, and will use certain rule sets to determine if you follow a best practice.
You need to install tfsec, and also here Chocolatey comes to the rescue. Run choco install tfsec to install latest version and add to path, all by using Chocolatey.
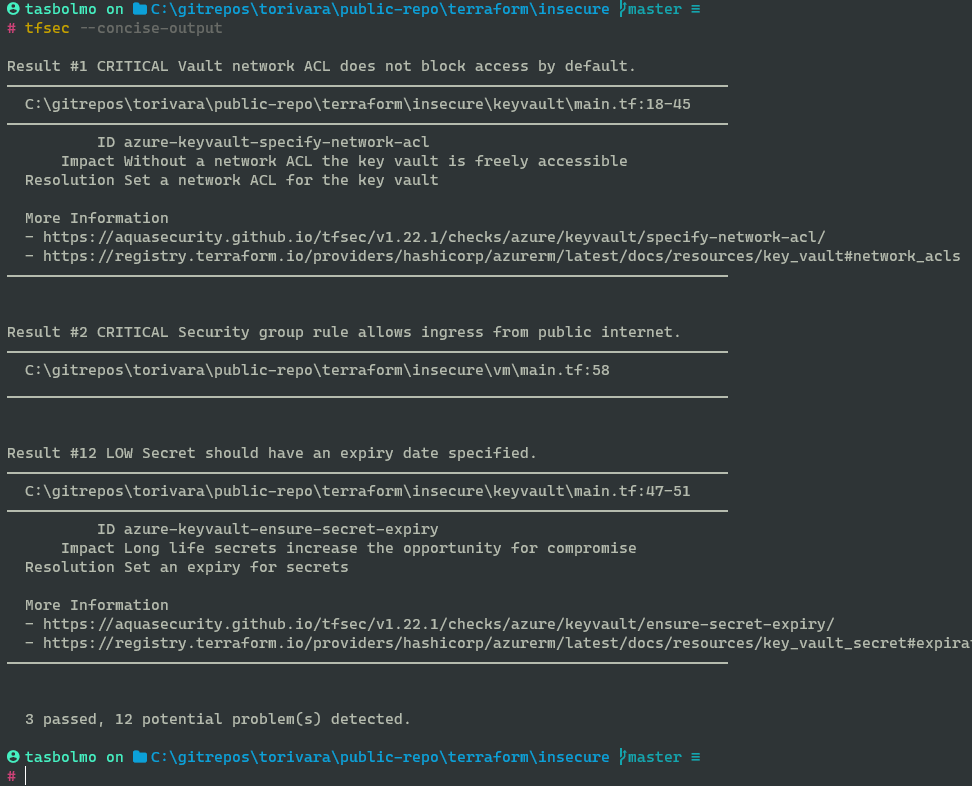
After you have tfsec installed, you can also run this from your command line directly.
When tfsec is available from your command line, you can start using the tfsec VSCode Extension. Open your VSCode, select Extensions, and download & install tfsec.
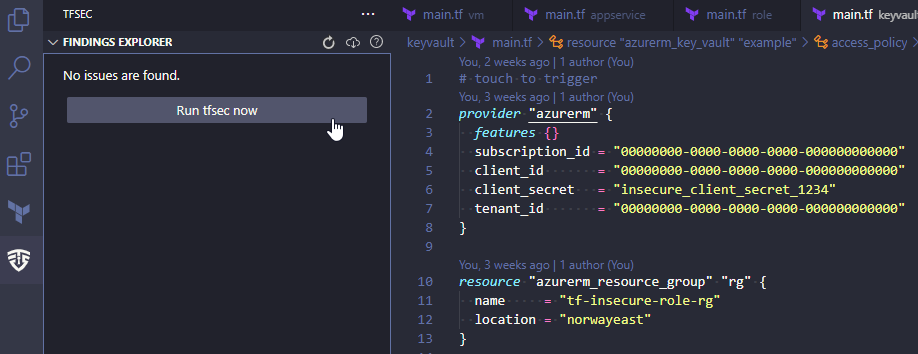
Run tfsec with your Terraform code open in VSCode.
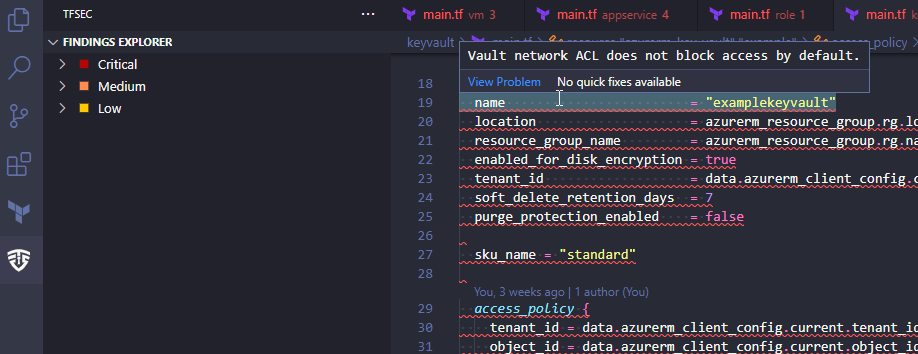
See the detected vulnerabilities.
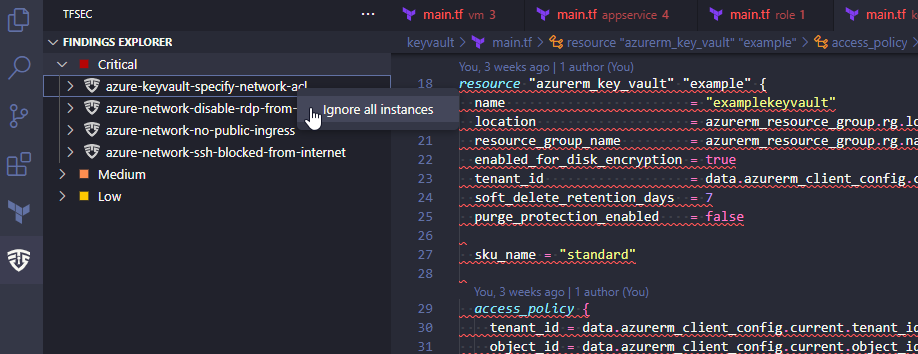
Exclusions
With tfsec you can also exclude certain findings. This is very easy, and results in a similar exclusion like we did with Checkov. Just right click the finding in the left window, and choose “Ignore all instances”.
This will add a comment like the below example.
#tfsec:ignore:azure-keyvault-specify-network-acl
resource "azurerm_key_vault" "example" {
name = "examplekeyvault"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
enabled_for_disk_encryption = true
tenant_id = data.azurerm_client_config.current.tenant_id
soft_delete_retention_days = 7
purge_protection_enabled = false
}
More testing
Checkov provides a few “insecure by design” examples that could be interesting to check. You can find them here in their blog post for the VSCode extension along with some more good information. I also provide a list below.
In summary
You have now learned how to use a pair of common IDE security extensions. You might also have discovered that there is such a thing as security vulnerability scanning directly in your IDE. In any case, I hope this was relevant and interesting, and thank you for reading this far.
There will be more DevSecOps tips and tricks here going forward 😎