IaC scanning with KICS
TL;DR
Just recently discovered KICS, and it simplifies scanning your IaC for misconfigurations or security issues. You can find more information here.
Keeping Infrastructure as Code secure (KICS)
“keeping infrastructure as code secure is an open source solution for static code analysis of Infrastructure as Code.”
KICS is a tool that can scan your IaC for vulnerabilities or erroneous configurations. It can scan Terraform, Kubernetes, Docker, Ansible, CloudFormation, ARM, Serverless, Pulumi, and more. It can also scan your code for secrets, and has a built-in secrets database. It can be used in your CI/CD pipelines, or directly on your workstation with docker. It also has a VSCode extension that can scan your code as you write it.
Running KICS in docker
First make sure you can run docker containers on your workstation. This can be tricky on Windows, but only if your workstation is managed by a large organization. If you are in control of your own workstation, you should be able to run docker containers without any issues.
The easiest way is to run Docker Desktop backed with WSL. Please be advised that Docker changed their licensing model some time ago, and you might need to buy a license if you are using it for commercial purposes within a large enterprise. Should be OK on your personal computer for non-commercial purposes.
Then you can run the following command to scan your IaC:
docker run -t -v {path_to_host_folder_to_scan}:/path checkmarx/kics:latest scan -p /path -o "/path/"
In my case I am running in WSL, and I want to scan a folder on my windows drive. Therefore I need to point the docker volume to my mounted c drive:
docker run -t -v /mnt/c/gitrepos/torivara/public-repo/terraform:/path checkmarx/kics:latest scan -p /path -o "/path/"
The first time you run this the docker image will be downloaded and it will take some additional time. Subsequent runs will be faster.
Some examples of results I got from my scan of an example Terraform folder. Mind you, some of these are vulnerable by design.
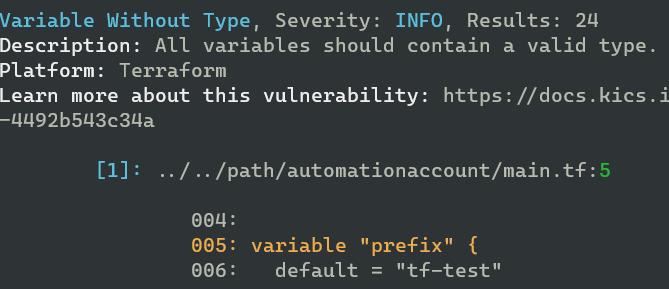
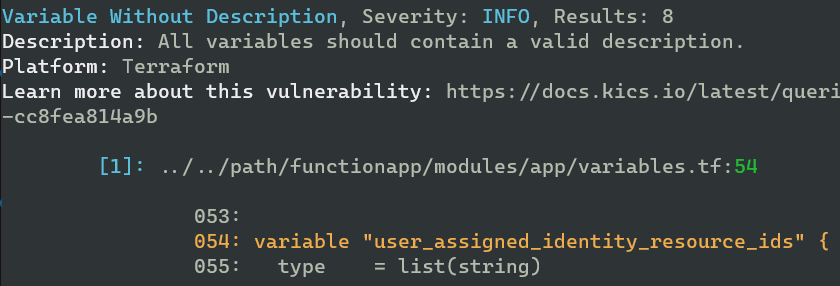
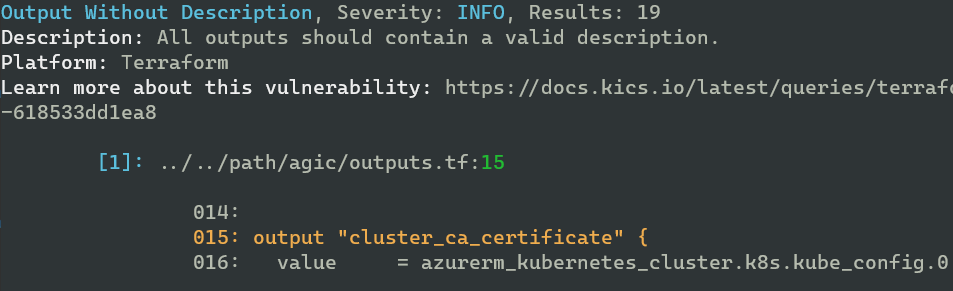
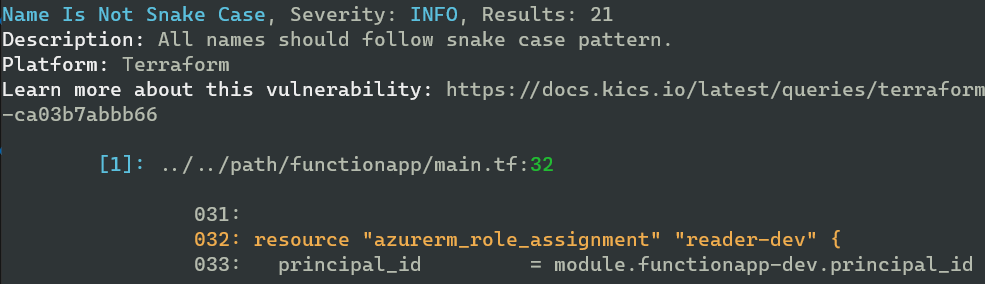
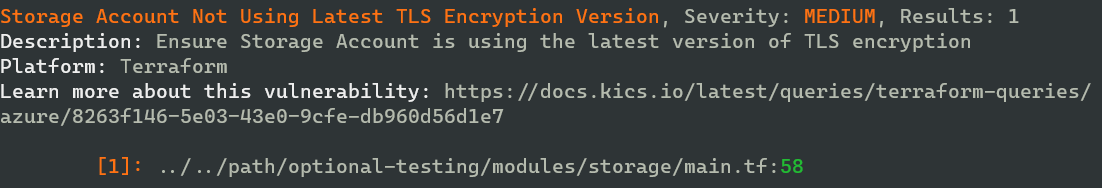
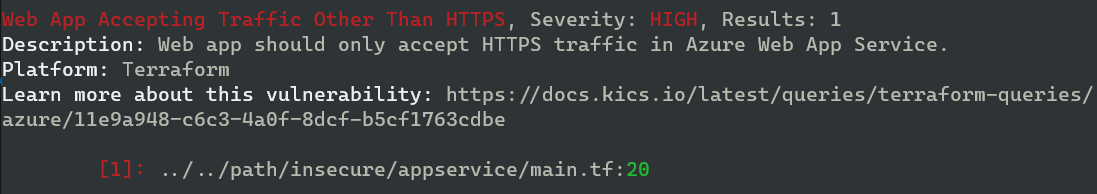
And as you can see, there are enough vulnerabilities to keep me busy for a while:
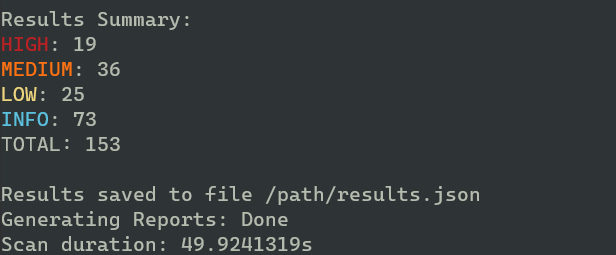
Running KICS in CI/CD
I mostly use GitHub for my personal projects, and therefore I will use GitHub Actions as an example. You can fond both Azure DevOps, Github Actions, Gitlab CI, Jenkins, and more on kics official page.
Create a new workflow in your .github folder, and add the following in your steps section:
- name: KICS Github Action
uses: Checkmarx/kics-github-action@v1.7.0
with:
# path to file or directory to scan
path: 'terraform' # this is my path for scanning. You might need to scan a different path.
You can see my full example here with more settings (SARIF, ignore_results, show results).
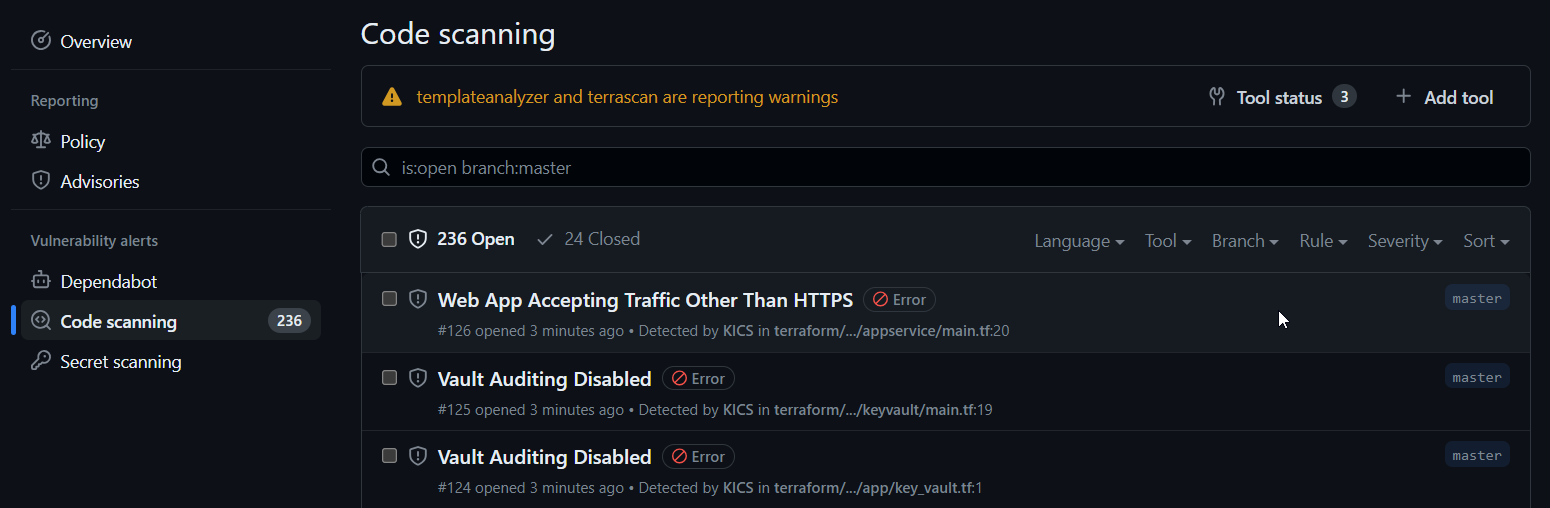
You can also store the results in an output folder, and upload them to the security page of your repository. This is done by adding an output_path parameter, and using the upload-sarif action.
SARIF is an acronym for Static Analysis Results Interchange Format, and is a standard for storing static analysis results. The standard format is supported by many other tools such as checkov, and also by GitHub code scanning.
Same result as when I ran it locally:
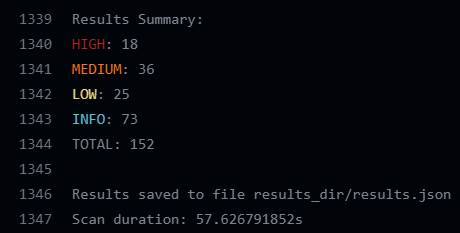
And the results are uploaded to the security tab of my repository:
Running KICS in VSCode
Just now I found out that you also can run KICS directly in VSCode. You can find more information here. After running KICS in a pipeline and in docker, I am not sure if I will use this feature, but it is nice to know that it is there. Docker is required locally, and I just don’t have that at the moment.
Install errors out for me because of missing docker atm. Still this is a nice touch, and I am sure it will be useful for many. Please see the installation instructions provided by Checkmarx. No login or extra configuration is required.
In summary
You should be doing whatever possible to improve the security of your DevSecOps workflow. KICS is a nice, simple tool which can help you secure IaC in all phases of development. It is easy to use, and can be integrated in your CI/CD pipelines. Usage directly in VSCode is also a possibility. I will definitely be using this tool in the future!